City government email scam targets crypto users nationwide
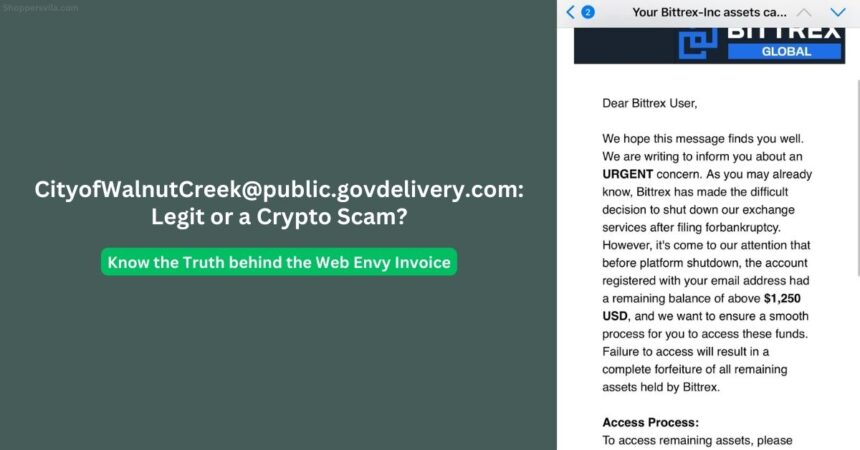
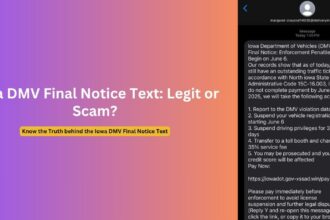
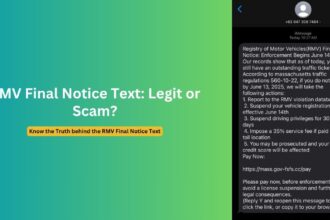
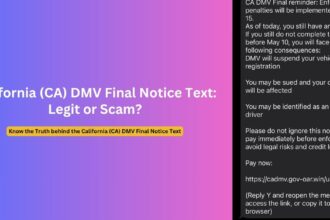
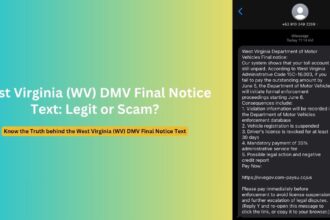
Last Thursday, I opened my inbox to find an email from [email protected] claiming I needed to take urgent action regarding cryptocurrency assets. As someone who had previously used platforms like Bittrex and BlockFi, my interest was immediately piqued. The message referenced a “final withdrawal period” and included official-looking government seals. For a brief moment, I wondered if this could be legitimate—perhaps related to some settlement I wasn’t aware of?
That fleeting moment of hope quickly gave way to suspicion. As I investigated further, what I discovered was an elaborate phishing operation targeting cryptocurrency users across the country. This article details my experience with this scam, how to identify it, and what steps to take if you’ve received similar communications.
The Email That Landed in My Inbox from [email protected]
The message appeared official at first glance—it featured what looked like a government header and used language that mimicked official communications. The sender, “[email protected],” seemed potentially legitimate since many government entities do use the govdelivery.com domain for mass communications.
The email claimed I was eligible for a “convenience class withdrawal” related to cryptocurrency holdings. It mentioned deadlines, referenced regulatory compliance, and created a sense of urgency with phrases like “final opportunity” and “required action.” A prominent button invited me to “Verify Eligibility and Process Withdrawal.”
What made this particularly convincing was how it blended truth with fiction. It referenced actual events—such as the Bittrex exchange closure or BlockFi bankruptcy proceedings—giving the communication a veneer of authenticity. The scammers had clearly done their homework, targeting users of specific cryptocurrency platforms that had experienced well-publicized issues.
Anatomy of the CityofWalnutCreek Email Scam
After researching online and consulting with cybersecurity experts, I learned this scam follows a sophisticated template:
- Government impersonation: The scammers use the name of a real municipal government (Walnut Creek, California) to establish legitimacy. The govdelivery.com domain portion is particularly clever since this is actually a legitimate service used by many government entities for email communications.
- Targeted victim selection: Rather than casting a wide net, these phishers specifically target cryptocurrency users who may have had accounts on troubled exchanges or platforms. This suggests they are either purchasing data from breaches or scraping information from public sources.
- Exploiting regulatory confusion: The cryptocurrency space is notoriously complex when it comes to regulations and legal proceedings. The scammers exploit this confusion by presenting themselves as part of an official process that victims may not fully understand.
- Creating artificial urgency: By establishing tight deadlines for action, the scammers pressure recipients into making quick decisions without proper verification.
The end goal is always the same: to direct victims to a convincing but fraudulent website where they will be asked to “verify their wallet” or “connect to claim funds.” Once a user connects their cryptocurrency wallet to these malicious sites, the attackers can drain their accounts within seconds.
How These Scammers Successfully Trap Victims
Through my investigation, I identified several psychological tactics these scammers employ to increase their success rate:
- Exploiting loss aversion: Many cryptocurrency users who experienced losses through platform bankruptcies or closures are desperate to recover whatever funds they can. This desperation can override normal caution.
- Authority bias: By impersonating government entities, scammers tap into our tendency to comply with perceived authority figures. The “City of Walnut Creek” branding lends an air of legitimacy that bypasses many people’s initial skepticism.
- Social proof manipulation: The scammers often create fake testimonials or forum posts discussing “successful withdrawals” to convince others the process is legitimate.
- Technical intimidation: Cryptocurrency processes can be technically complex. Scammers use this to their advantage by creating convoluted “verification procedures” that seem plausible to those unfamiliar with how blockchain transactions actually work.
- Manufactured scarcity: Phrases like “limited withdrawal window” create the impression that victims must act immediately or lose their opportunity forever.
What makes these attacks particularly effective is their tailoring to specific cryptocurrency communities. For instance, victims of the Bittrex exchange closure or BlockFi bankruptcy are already primed to expect some form of claims process. The scammers simply insert themselves into that expectation.
Red Flags That Exposed the [email protected] Scam
After my initial concern, several elements raised my suspicions about this email:
- Jurisdictional nonsense: Why would the City of Walnut Creek in California be handling cryptocurrency matters related to a global exchange or lending platform? Government responsibilities simply don’t work this way—cryptocurrency regulation occurs at federal levels through agencies like the SEC, CFTC, or Treasury Department, not through local municipalities.
- Domain inconsistencies: While the “govdelivery.com” portion looked somewhat legitimate, the complete email address structure was unusual. Legitimate government communications typically use clear department identifiers.
- Verification link URL: Hovering over the “Verify Eligibility” button revealed a suspicious URL that had nothing to do with either Walnut Creek or legitimate government domains. Instead, it pointed to domains like “verify-328713-bittrex.com” or similar suspicious variants.
- Generic salutation: The email began with “Dear User” rather than my actual name, despite claiming to be about my specific accounts.
- Pressure tactics: The emphasis on “final opportunity” and tight deadlines is characteristic of scam attempts, not legitimate government processes which typically provide reasonable timeframes.
- Requested action: Most critically, the site wanted me to connect my cryptocurrency wallet directly—something no legitimate government claims process would ever require.
After noticing these red flags, I searched online and found Reddit discussions confirming my suspicions: this was indeed a widespread phishing campaign targeting cryptocurrency users.
What To Do If You Receive This Email from [email protected]
If you’ve received an email from “[email protected]” or similar suspicious senders, follow these steps:
- Do not click any links in the email. This is paramount—even visiting the website without entering information can sometimes expose you to certain types of malware.
- Report the phishing attempt to:
- The FBI’s Internet Crime Complaint Center (IC3) at www.ic3.gov
- The Federal Trade Commission at ReportFraud.ftc.gov
- The Anti-Phishing Working Group at [email protected]
- Forward the email to [email protected] and [email protected]
- Alert the impersonated entities:
- Report to the actual City of Walnut Creek through their official website
- If cryptocurrency platforms are mentioned (like Bittrex or BlockFi), inform their security teams through official channels
- Warn others in cryptocurrency communities on platforms like Reddit, Twitter, and Discord to help spread awareness.
- Update your security measures as a precaution:
- Change passwords for cryptocurrency exchanges and wallets
- Enable two-factor authentication if you haven’t already
- Consider moving assets to cold storage if they’re currently on exchanges
If you’re awaiting legitimate information about cryptocurrency platform bankruptcies or closures, always verify through official channels by manually typing the known website addresses rather than following email links.
Protecting Yourself From Crypto Phishing Scams
After my experience, I’ve implemented several security practices that all cryptocurrency users should consider:
- Verify through official channels only: For matters related to Bittrex, BlockFi, or other cryptocurrency platforms, only use information from:
- Their official websites (accessed by typing the URL directly, not through links)
- Court-approved bankruptcy notices (through PACER or official case websites)
- Communications sent from previously established and verified email addresses
- Create a separate email for cryptocurrency: Consider using a dedicated email address for cryptocurrency activities to isolate potential phishing attempts from your primary accounts.
- Use advanced wallet security:
- Hardware wallets provide significant protection against phishing
- Multi-signature requirements for transactions add an additional security layer
- Consider whitelist-only withdrawals on exchanges that offer this feature
- Implement robust verification practices:
- Call official numbers (found on legitimate websites) to verify communications
- Check social media accounts of companies for announcements about official processes
- Consult with knowledgeable community members before taking action on unexpected communications
- Stay informed about ongoing scams by following:
- The FTC’s scam alert page
- Cryptocurrency security blogs and newsletters
- Community forums like r/CryptoCurrency or platform-specific subreddits
Remember that legitimate bankruptcy proceedings and regulatory actions move slowly and follow established legal patterns. They never require connecting cryptocurrency wallets to random websites or sharing private keys.
If You’ve Already Fallen Victim to the Scam
If you’ve interacted with this scam by clicking links or, worse, connecting your wallet, immediate action is crucial:
- Secure remaining assets immediately:
- Create a new wallet with completely different recovery phrases
- Transfer any cryptocurrency from potentially compromised wallets to this new secure wallet
- Disconnect any wallet connections authorized through suspicious websites
- Document everything for reporting:
- Take screenshots of the phishing email
- Capture the fraudulent website (if safe to do so)
- Record any transaction hashes for unauthorized transfers
- Note timestamps of all relevant events
- Report the theft to:
- Local law enforcement (file a police report)
- FBI’s Internet Crime Complaint Center
- The exchange or platform where your wallet was hosted
- Blockchain forensics companies like Chainalysis or CipherTrace
- Protect your wider digital identity:
- Change passwords across all financial accounts
- Check credit reports for suspicious activity
- Consider placing a credit freeze if personal information was compromised
- Monitor accounts for unusual login attempts
While cryptocurrency theft is notoriously difficult to recover from due to the irreversible nature of blockchain transactions, reporting helps authorities track patterns and occasionally leads to the identification of perpetrators.
The Evolving Landscape of Cryptocurrency Scams
This CityofWalnutCreek phishing campaign represents a concerning evolution in cryptocurrency scams. Rather than obvious “too good to be true” schemes, these sophisticated operations mimic legitimate processes that users might reasonably expect to encounter.
As cryptocurrency adoption increases, we can anticipate several trends in phishing attempts:
- Increased targeting of distressed platform users: Users of bankrupt or troubled exchanges will continue to be primary targets.
- More sophisticated impersonation: Government agencies, law firms handling bankruptcy proceedings, and claims administrators will all be impersonated with increasing technical sophistication.
- Cross-platform coordination: Expect scammers to create entire ecosystems of fake verification, including fraudulent social media accounts, forged documents, and even fake “verification” phone lines.
The most effective defense against these evolving threats remains education and community vigilance. By sharing experiences like mine, we create collective knowledge that helps protect vulnerable users from falling victim to these schemes.
My close call with the CityofWalnutCreek phishing attempt was a stark reminder that in the cryptocurrency space, verification is not optional—it’s essential. By maintaining healthy skepticism and following proper security practices, we can protect ourselves from even the most convincing scams.
Remember: no legitimate government agency or bankruptcy proceeding will ever ask you to connect your cryptocurrency wallet to verify your identity or claim funds. When in doubt, verify independently through official channels, and never allow urgency to override security.