A new wave of sophisticated phishing attacks is targeting users with fraudulent PayPal notifications sent through DocuSign, featuring the fake identity “Jennifer Muth” and originating from suspicious “@lifexty.site” email addresses. This latest variant in the ongoing DocuSign-PayPal scam epidemic represents an escalation in tactics, combining trusted platform abuse with deceptive sender identities to bypass security measures and steal sensitive financial information.
Security researchers are warning that these “Jennifer Muth” emails are part of a coordinated campaign that has already affected thousands of users worldwide, exploiting DocuSign’s reputation for legitimate business communications while masquerading as PayPal customer service representatives.
Understanding the Jennifer Muth DocuSign Scam Campaign
The “Jennifer Muth” phishing campaign represents a sophisticated evolution of DocuSign-based PayPal scams that have plagued users since early 2025. Unlike previous variants that used generic sender names or obviously fake identities, this campaign employs specific personas like “Jennifer Muth” to create an illusion of personalized customer service.
What makes this particular scam especially dangerous is its multi-layered deception. The emails appear to originate from DocuSign’s trusted infrastructure while claiming to represent PayPal customer service. However, careful analysis reveals that these messages actually come from suspicious domains like “lifexty.site” – a clear red flag that many users overlook due to the professional presentation and DocuSign branding.
Cybersecurity expert Dr. Sarah Mitchell explains, “The Jennifer Muth campaign shows how scammers are becoming more sophisticated in their social engineering. By using specific names and professional presentation, they’re creating a false sense of legitimacy that can fool even security-conscious users.”
The campaign has been particularly active since March 2025, with security forums reporting hundreds of incidents involving similar email patterns. One IT administrator noted receiving reports from 15 different employees within a single week, all involving emails from “Jennifer Muth” claiming to represent PayPal customer service through DocuSign communications.
Comprehensive Overview of the DocuSign-PayPal Scam Ecosystem
The Jennifer Muth emails are part of a broader ecosystem of DocuSign-based phishing attacks that have evolved significantly since their emergence. These scams exploit the trust users place in DocuSign as a legitimate business platform, combined with the urgency typically associated with financial security notifications.
Recent analysis by cybersecurity firms shows that DocuSign-based phishing attacks have increased by over 400% in the first quarter of 2025 compared to the same period in 2024. The scams typically follow these common characteristics:
- Platform Abuse: Using legitimate DocuSign infrastructure to deliver malicious content
- Brand Impersonation: Claiming to represent well-known financial services like PayPal
- Social Engineering: Creating false urgency around account security or unauthorized transactions
- Multi-Channel Attacks: Combining email communications with phone-based follow-up attempts
The Jennifer Muth variant specifically targets users with fabricated PayPal account alerts, often claiming suspicious cryptocurrency transactions or unauthorized purchases. What distinguishes this campaign is its use of the “@lifexty.site” domain, which attempts to appear legitimate while actually serving as a staging ground for credential harvesting and further social engineering attacks.
Security researcher Marcus Chen notes, “We’re seeing a clear pattern where attackers are moving away from obviously suspicious domains toward ones that might appear legitimate at first glance. The ‘lifexty.site’ domain is designed to sound corporate and trustworthy, which is part of the psychological manipulation.”
Detailed Analysis: How the Jennifer Muth Paypal Fraud Operates
The Jennifer Muth DocuSign scam follows a carefully orchestrated multi-stage process designed to maximize success rates while minimizing detection:
Stage 1: Initial Contact and Trust Building
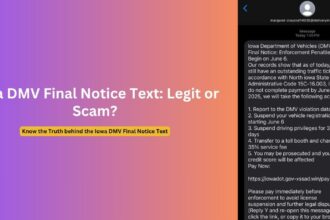
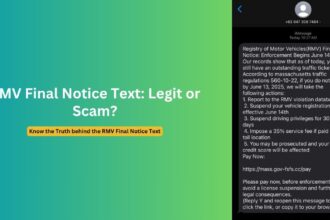
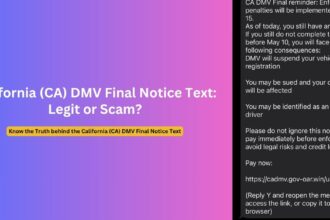
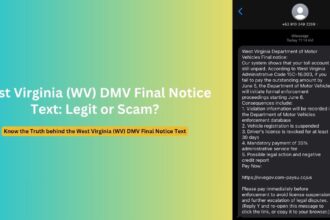
The attack begins with an email appearing to come from “Jennifer Muth” via DocuSign, typically with a professional-looking signature identifying her as a PayPal customer service representative. The email claims to be notifying the recipient about suspicious account activity, usually involving cryptocurrency transactions ranging from $599 to $899.
Stage 2: Urgency Creation
The message creates immediate concern by claiming the recipient’s PayPal account shows unauthorized Bitcoin purchases or suspicious international transactions. The email emphasizes that the account has been “temporarily suspended for protection” and requires immediate action to prevent further unauthorized activity.
Stage 3: DocuSign Legitimacy Exploitation
Rather than directly requesting credentials, the email directs users to click a “REVIEW DOCUMENT” button that leads to an actual DocuSign page. This intermediate step serves multiple purposes:
- It appears to validate the communication as legitimate business correspondence
- It helps bypass email security filters that might flag direct phishing attempts
- It creates an additional layer of perceived authenticity
Stage 4: Information Harvesting
Once users access the DocuSign document, they encounter forms requesting “verification” of their PayPal account details, including login credentials, security questions, and sometimes banking information. The forms are professionally designed to mimic legitimate PayPal interfaces.
Stage 5: Phone-Based Social Engineering
Many recipients report receiving follow-up phone calls from individuals claiming to be PayPal security representatives, often referencing the DocuSign document and requesting additional verification steps that may include remote access to the victim’s device.
One victim described their experience: “The email looked completely professional, and when I saw the DocuSign branding, I thought it was legitimate. It wasn’t until I started getting repeated phone calls asking for more personal information that I realized something was wrong.”
Identifying Fake Email Patterns in Jennifer Muth Communications
The Jennifer Muth phishing emails follow distinct patterns that can help users identify them as fraudulent:
Email Header Analysis
- From Address: Typically shows “@lifexty.site” domain rather than official PayPal or DocuSign domains
- Display Name: Shows “Jennifer Muth” or variations like “Jennifer Muth – PayPal Customer Service”
- Reply-To Address: Often differs from the sending address and may include suspicious domains
Content Structure Patterns
- Subject Lines: Common themes include:
- “PayPal Account Security Alert – Action Required”
- “Suspicious Activity Detected on Your PayPal Account”
- “Urgent: Cryptocurrency Transaction Pending Verification”
- “PayPal Account Temporarily Restricted – Jennifer Muth”
- Body Content: Consistent elements include:
- Specific transaction amounts (commonly $599.00, $799.00, or $899.00)
- References to Bitcoin or cryptocurrency purchases
- Claims of transactions from “unfamiliar IP addresses”
- Professional language mixing PayPal and DocuSign terminology
Document Presentation
- DocuSign Integration: Uses actual DocuSign infrastructure to host malicious forms
- Professional Design: Mimics legitimate PayPal communication styles and branding
- Urgency Language: Emphasizes immediate action required to prevent account closure
- Contact Information: Provides toll-free phone numbers claiming to be PayPal support
Security analyst Lisa Rodriguez observes, “The sophistication of these emails is remarkable. They’ve clearly studied legitimate PayPal communications and DocuSign workflows to create nearly perfect replicas that can fool even experienced users.”
Critical Red Flags That Expose the Scam
Despite their sophisticated appearance, several warning signs can help users identify these fraudulent communications:
1. Domain Verification Issues
The most significant red flag is the “@lifexty.site” domain, which has no legitimate connection to either PayPal or DocuSign. Legitimate PayPal communications come from “@paypal.com” domains, while authentic DocuSign messages originate from “@docusign.com” or “@docusign.net.”
2. Unusual Communication Methods
PayPal does not typically use DocuSign to communicate about account security issues. The company has its own notification systems and would direct users to log into their accounts through official channels rather than third-party document platforms.
3. Cryptocurrency Transaction Focus
The heavy emphasis on cryptocurrency transactions is a deliberate psychological tactic. Most users don’t regularly purchase cryptocurrency, so such transactions immediately create alarm and urgency, potentially overriding careful consideration.
4. Generic Recipient Information
Many users report that the emails are addressed to generic names or email addresses that don’t match their actual PayPal account information, indicating mass distribution rather than personalized communication.
5. Pressure for Immediate Phone Contact
Legitimate financial institutions rarely instruct customers to call immediately about specific transactions. They typically direct users to secure online portals or mobile applications to review flagged activities.
6. Inconsistent Branding
While the emails attempt to mimic PayPal branding, careful examination often reveals inconsistencies in logos, fonts, or terminology that don’t match authentic PayPal communications.
Comprehensive Protection Strategies Against DocuSign-PayPal Scams
Protecting against these sophisticated attacks requires a multi-layered approach combining technical measures, behavioral changes, and organizational policies:
1. Email Security Enhancements
Domain Filtering: Implement email filters that flag messages from suspicious domains like “lifexty.site” or other non-standard business domains claiming to represent major financial institutions.
DocuSign Content Screening: Create specific rules to quarantine DocuSign messages containing PayPal-related keywords, cryptocurrency references, or urgent action language.
Authentication Verification: Always verify that DocuSign messages come from legitimate “@docusign.com” or “@docusign.net” domains before taking any action.
2. Account Security Measures
Multi-Factor Authentication: Enable MFA on both PayPal and DocuSign accounts to create additional security barriers even if credentials are compromised.
Regular Account Monitoring: Set up automatic notifications for all account activities, making it easier to quickly identify unauthorized access attempts.
Strong Password Policies: Use unique, complex passwords for each financial account, stored in a reputable password manager.
3. Verification Protocols
Independent Channel Verification: Never use contact information provided in suspicious emails. Instead, manually navigate to official websites or use known customer service numbers to verify any concerning account notifications.
Direct Account Access: Log into PayPal accounts directly through the official website or mobile app to check for any actual security alerts or transaction issues.
Document Authenticity Checks: Before engaging with any DocuSign document claiming to be from PayPal, verify its legitimacy through official PayPal customer service channels.
4. Organizational Training
Regular Security Awareness: Conduct ongoing training sessions highlighting current phishing trends, including examples of DocuSign-based attacks and the Jennifer Muth campaign specifically.
Incident Reporting Procedures: Establish clear protocols for employees to report suspicious emails without fear of consequences, creating a collaborative security environment.
Simulation Exercises: Implement controlled phishing simulations to test and improve organizational resilience against these sophisticated attacks.
Immediate Response Actions If You’ve Been Targeted
If you’ve interacted with a Jennifer Muth email or similar DocuSign-PayPal communications, take these critical steps immediately:
Immediate Security Measures
- Change All Passwords: Immediately update passwords for PayPal, DocuSign, and any other financial accounts using unique, strong passwords for each service.
- Enable Account Alerts: Activate all available security notifications for financial accounts to monitor for unauthorized activities.
- Contact Official Support: Report the incident directly through PayPal’s official fraud reporting system, accessible through their website or mobile app.
Investigation and Documentation
- Preserve Evidence: Save copies of the suspicious emails and any related communications for potential law enforcement reporting.
- Review Account Activities: Carefully examine recent transactions and account activities across all financial services for signs of unauthorized access.
- Check Credit Reports: Monitor credit reports for unexpected account openings or credit inquiries that might indicate identity theft.
System Security Actions
- Complete Malware Scan: Run comprehensive security scans on all devices used to access the suspicious emails or communicate with potential scammers.
- Update Security Software: Ensure all antivirus and anti-malware programs are current and configured for real-time protection.
- Network Security Review: Consider changing Wi-Fi passwords and reviewing network security settings if scammers potentially gained device access.
Financial Protection Measures
- Fraud Alert Placement: Consider placing fraud alerts with major credit bureaus to add extra verification requirements for new credit applications.
- Bank Notification: Inform banks and credit card companies about potential compromise to enable enhanced monitoring of account activities.
- Transaction Monitoring: Increase vigilance in monitoring all financial transactions for several months following the incident.
Frequently Asked Questions (FAQs)
1. Is any email from Jennifer Muth representing PayPal customer service legitimate?
No. PayPal does not currently have a customer service representative named “Jennifer Muth” who sends DocuSign communications about account security. This name appears to be entirely fabricated for this phishing campaign, and any emails claiming to be from this individual should be considered fraudulent.
2. Why do these scam emails come from “@lifexty.site” instead of PayPal domains?
The “@lifexty.site” domain is used by scammers to host their phishing infrastructure while attempting to appear legitimate. They cannot use actual PayPal domains (@paypal.com) because they don’t control PayPal’s email systems. The unfamiliar domain is actually one of the strongest indicators that these emails are fraudulent.
3. Can DocuSign prevent these scams from using their platform?
While DocuSign has security measures in place and actively works to combat platform abuse, the scale of their service makes it challenging to prevent all malicious use. They encourage users to report suspicious emails to [email protected] and have developed resources to help users identify fraudulent communications that abuse their platform.
4. What information are these Jennifer Muth scams trying to collect?
These scams primarily target PayPal login credentials, personal identification information, banking details, and security question answers. Some variants also attempt to establish phone contact for more extensive social engineering, potentially seeking remote access to victims’ devices or attempting to convince them to make direct payments.
5. How can I tell if a DocuSign email about PayPal is legitimate?
Legitimate PayPal communications rarely use DocuSign for account security matters. Always verify by: (1) checking that the email comes from official @paypal.com or @docusign.com domains, (2) logging into your PayPal account independently to check for alerts, (3) contacting PayPal customer service directly using official contact methods, and (4) being suspicious of any urgent cryptocurrency-related transaction claims.
The Evolving Threat Landscape and Future Implications
The Jennifer Muth campaign represents a concerning evolution in phishing sophistication that has broader implications for cybersecurity. By combining trusted platform abuse with personalized social engineering and multi-channel attack vectors, criminals are creating scenarios where traditional security awareness training may be insufficient.
Security researchers are particularly concerned about the trend toward using specific fabricated identities like “Jennifer Muth” rather than generic sender names. This personalization creates a false sense of relationship and trust that can be especially effective against users who may have previous legitimate interactions with customer service representatives.
The use of domains like “lifexty.site” also represents a shift toward more sophisticated domain selection. Rather than using obviously suspicious domains, attackers are choosing names that might sound corporate or legitimate to casual observation, requiring users to be more vigilant about domain verification.
Dr. Amanda Foster, a cybersecurity researcher at Digital Security Institute, warns, “We’re seeing attackers invest more time and resources into creating believable personas and infrastructure. The days when we could rely on obvious spelling errors or suspicious domains to identify phishing attempts are rapidly ending.”
This evolution suggests that future security training must emphasize verification protocols and independent authentication methods rather than relying solely on red flag identification, as the red flags are becoming increasingly subtle and sophisticated.
Conclusion
The Jennifer Muth PayPal-DocuSign phishing campaign demonstrates the rapidly evolving nature of cyber threats and the need for equally sophisticated defense strategies. As attackers continue to abuse trusted platforms and develop more convincing social engineering techniques, users and organizations must adapt their security approaches accordingly.
The key to protection lies not just in identifying red flags, but in establishing robust verification protocols that don’t rely on the apparent legitimacy of communications. When financial security is at stake, the safest approach is always to independently verify any concerning notifications through official channels rather than responding to unsolicited communications, regardless of how professional they appear.
As these attacks continue to evolve, staying informed about current threat patterns and maintaining healthy skepticism about unexpected financial communications remains crucial. The Jennifer Muth campaign serves as a powerful reminder that in cybersecurity, vigilance and verification are always preferable to trust and convenience.
Organizations and individuals who implement comprehensive security measures, including technical controls, ongoing education, and robust incident response procedures, will be best positioned to defend against these increasingly sophisticated threats.
For the latest updates on emerging cybersecurity threats and protection strategies, visit shoppersvila.com’s security resource center and subscribe to threat intelligence updates.
Disclaimer: This article is provided for educational and informational purposes only. Threat indicators and attack methods may evolve as criminals adapt their techniques. Always consult with cybersecurity professionals for specific security recommendations.