Cryptocurrency investors across multiple platforms have recently been targeted by sophisticated phishing attempts from email addresses ending in “public.govdelivery.com” – particularly “[email protected]” and similar variations. These emails claim to represent bankruptcy proceedings for cryptocurrency exchanges like Bittrex and BlockFi, offering identical compensation amounts to thousands of recipients. This article investigates the legitimacy of these communications, how to identify them, and steps to protect yourself from these increasingly sophisticated scams.
The [email protected] Email Campaign
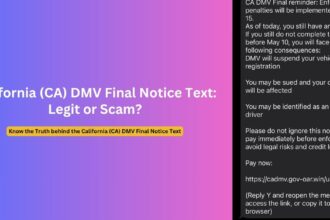
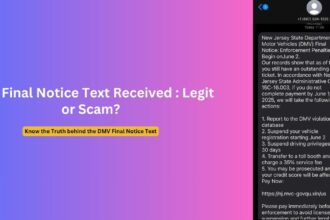
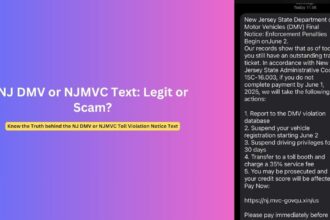
In recent weeks, thousands of cryptocurrency investors have reported receiving emails from “[email protected]” claiming to represent Omni Agent Solutions in relation to Bittrex cryptocurrency exchange’s bankruptcy proceedings. The emails state recipients are entitled to exactly $3,192.51 in compensation and direct them to a link for their “account overview” to access these supposed funds.
These communications are part of a coordinated phishing campaign exploiting legitimate government email infrastructure to add credibility to their fraudulent messages. The “donaanactynm” portion of the address references Doña Ana County in New Mexico, a legitimate local government entity, while the “govdelivery.com” domain belongs to a legitimate communications platform used by many U.S. government agencies.
The timing of these emails is particularly calculated, as they coincide with actual bankruptcy proceedings for cryptocurrency exchanges, creating a plausible context that makes recipients more likely to engage with the fraudulent messages.
Overview of GovDelivery-Based Crypto Scams
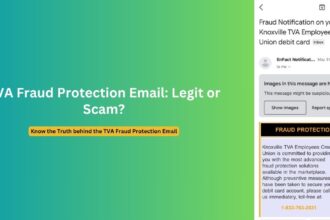
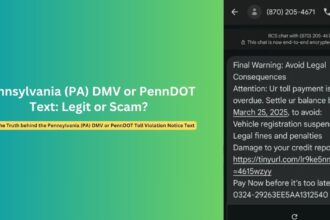
This current campaign represents an evolution of cryptocurrency phishing tactics that have been observed for several years. Similar scams using the govdelivery.com domain have targeted users across multiple cryptocurrency platforms:
Multiple Platform Targeting
The scammers have sent nearly identical messages to users of:
- Bittrex (with identical claims of $3,192.51)
- BlockFi (with identical claims of $4,163.71)
- Other cryptocurrency exchanges whose user data has been compromised
Evolution of Techniques
Evidence from Reddit and other online forums indicates these tactics have been refined over time:
- Three years ago, similar govdelivery.com addresses were used to impersonate Microsoft for password reset scams
- More recently, the scammers have shifted focus to cryptocurrency bankruptcy proceedings
- The level of sophistication in mimicking legitimate communications has increased dramatically
Exploitation of GovDelivery Infrastructure
The scammers appear to be exploiting vulnerabilities in the GovDelivery platform (now owned by Granicus) that allows them to:
- Send emails that pass standard email security protocols (SPF, DKIM, and DMARC checks)
- Utilize legitimate government domain infrastructure to enhance credibility
- Potentially leverage actual security breaches in municipal systems
The common thread across these campaigns is the misuse of govdelivery.com domains, suggesting a systematic exploitation of this platform’s trust and security to execute sophisticated phishing operations.
How the [email protected] Scam Works
The operation follows a calculated process designed to harvest cryptocurrency credentials:
1. Initial Contact
Victims receive an email from addresses like “[email protected]” claiming to represent either:
- Omni Agent Solutions for Bittrex bankruptcy proceedings
- Kroll Restructuring Administration for BlockFi bankruptcy cases
2. False Claims
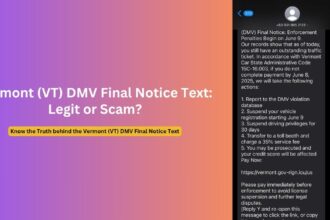
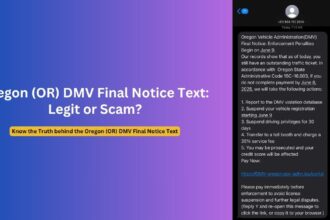
The email informs recipients they’re entitled to receive a specific amount as part of their “remaining claim” – always exactly $3,192.51 for Bittrex claims or $4,163.71 for BlockFi claims, regardless of the recipient’s actual account history.
3. Deceptive Links
The email contains links to a supposed “account overview” or “payment platform” where victims can claim their funds.
4. Credential Harvesting
Upon following the link, victims encounter a professional-looking interface that requests:
- Email address verification
- Connection of a cryptocurrency wallet
- Entry of wallet seed phrases or private keys (the critical piece of information that gives complete access to cryptocurrency holdings)
5. Fund Theft
If victims provide these credentials, scammers gain complete control of their cryptocurrency wallets, allowing them to:
- Transfer all cryptocurrency assets to their own wallets
- Access multiple cryptocurrency platforms if the victim reuses the same wallet
- Potentially steal additional personal and financial information
As one Reddit user who investigated the scam noted: “When you proceed to ‘attempt’ to withdraw the fictitious $3,192.51, the redemption link directs you to connect to your preferred wallet to withdraw your funds. NEVER SEND YOUR WALLET SECRET PHRASES TO ANYONE.”
Email Patterns and Key Characteristics
These fraudulent emails follow consistent patterns that help identify them as part of coordinated campaigns:
Sender Information
The emails consistently use various govdelivery.com addresses:
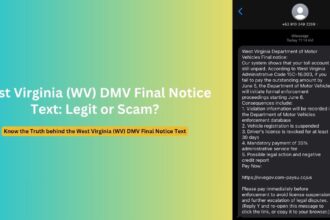
- “[email protected]” (referencing Doña Ana County, NM)
- “[email protected]” (referencing Agoura Hills, CA)
- “[email protected]” (possibly referencing Library of Congress)
Content Elements
The emails typically include:
- References to legitimate bankruptcy administrators (Omni Agent Solutions, Kroll)
- Claims of court authorization and official case administration
- Identical compensation amounts across all recipients ($3,192.51 for Bittrex or $4,163.71 for BlockFi)
- Generic greetings like “Dear Valued Customer” rather than personalized names
- Urgency language encouraging immediate action
- Official-looking formatting and letterhead
Link Destinations
The links direct to sophisticated phishing sites featuring:
- Professional interfaces mimicking legitimate payment platforms
- Requests to “verify identity” with email addresses and identification codes
- Wallet connection interfaces that request seed phrases or private keys
- Broken navigation links that don’t function properly
- Multiple redirect chains through URL shorteners and intermediate domains
Red Flags Exposing the Scam
Several telltale signs clearly identify these communications as fraudulent:
1. Identical Claim Amounts
The most obvious indicator is the identical compensation amount reported by all recipients:
- $3,192.51 for Bittrex-related emails
- $4,163.71 for BlockFi-related emails
As one Reddit user commented: “Same amount here. Scam. Guess they divided the funds equally among us! 😂😭”
2. Unrelated Government Email Domains
Legitimate bankruptcy administrators would never communicate through:
- Local government email domains like Doña Ana County, NM or Agoura Hills, CA
- Public government communication platforms unrelated to bankruptcy proceedings
3. Spelling and Name Errors
The Bittrex scam emails contain subtle errors like:
- “Omni Agent SoIutions” with a capital “I” instead of “L”
- References to “Bittrex International” instead of the correct “Bittrex Global”
4. Generic Greetings
Despite cryptocurrency exchanges requiring identity verification, the emails use impersonal greetings. As one Reddit user explained: “‘Valued Customer’ is a dead giveaway for a scam. Any company who you have done business with would at the very least use your first name.”
5. Identical Payee IDs
Multiple recipients report receiving the exact same identification codes:
- Same Payee ID for BlockFi claims: “9QFM-QXWN-YMTE-S5Q4”
- Same Account IDs for Bittrex claims
6. Request for Wallet Seed Phrases
Legitimate bankruptcy administrators would never request:
- Connection of cryptocurrency wallets
- Seed phrases or private keys
- Installation of specific wallet applications
As the real Kroll Restructuring Administration states on their website: “Please be advised that Kroll Restructuring Administration will never ask or require you to…link a cryptocurrency wallet to a website or application [or] provide your seed phrase or private keys.”
How to Identify and Protect Yourself
Protecting yourself from these sophisticated scams requires vigilance and adherence to security best practices:
Immediate Steps If You Received the Email
- Do Not Click Links: Never click links in unexpected emails claiming you’re owed cryptocurrency, especially from unfamiliar or government-related email addresses.
- Report as Phishing: Mark the email as phishing in your email client to help protect others.
- Verify Through Official Channels: If you believe you might legitimately be owed funds, visit the official bankruptcy case website directly by typing the URL yourself (not from the email).
- Check Community Forums: Search for information about suspicious emails on Reddit and other cryptocurrency forums – community discussions often quickly identify scams.
Essential Security Practices
- Never Share Seed Phrases: Legitimate companies will never ask for your wallet’s seed phrase or private keys—these should be kept completely private.
- Verify Official Email Addresses: Legitimate bankruptcy communications come from specific, verified email domains:
- For Kroll: [email protected] or [email protected]
- For Omni Agent Solutions: direct domain emails, not government forwarding addresses
- Be Skeptical of Identical Amounts: If online discussions reveal others receiving identical compensation amounts, it’s almost certainly fraudulent.
- Use Hardware Wallets: Hardware wallets provide an additional layer of protection requiring physical confirmation of transactions.
- Enable 2FA Everywhere: Use two-factor authentication on all cryptocurrency platforms and email accounts.
Is [email protected] Email Legit?
No, emails from [email protected] are not legitimate bankruptcy communications. This is a fraudulent email address being used in a sophisticated phishing campaign. There are several definitive reasons why these emails should be considered illegitimate:
- Misused Government Infrastructure: The “donaanactynm” portion refers to Doña Ana County in New Mexico, which has no legitimate connection to cryptocurrency bankruptcy proceedings. GovDelivery (now Granicus) is a legitimate communications platform used by government agencies, but these emails represent either:
- Complete spoofing of the address
- Exploitation of security vulnerabilities in the GovDelivery platform
- Compromise of actual government accounts
- Inconsistent with Official Communications: Legitimate bankruptcy administrators have established specific email domains for communications and have publicly stated they will never request cryptocurrency wallet connections or seed phrases.
- Universal Red Flags: The identical compensation amounts, generic greetings, and suspicious links demonstrate classic phishing tactics.
- Community Confirmation: Thousands of recipients across cryptocurrency forums have confirmed receiving identical emails with the same dollar amounts and payee IDs, mathematically impossible in legitimate bankruptcy distributions.
As one security-focused Reddit user summarized: “This email was sent to [my_email_address] using GovDelivery Communications Cloud on behalf of: City of Agoura Hills, California… it has a phone number – did anybody call this number?” These details further confirm the fraudulent nature of the communication.
Frequently Asked Questions
1. Received Email from [email protected]. Is it Real or Fake?
No, the email from [email protected] is not legitimate. It is part of a sophisticated phishing campaign targeting cryptocurrency investors. The email address combines Doña Ana County, New Mexico references with the GovDelivery platform to appear official, but it has no legitimate connection to cryptocurrency bankruptcy proceedings. Legitimate administrators use specific company domains for communications, not local government email addresses.
2. What is GovDelivery and why are scammers using it?
GovDelivery (now owned by Granicus) is a legitimate communications platform used by many U.S. government agencies to send notifications and updates to citizens. Scammers are exploiting this platform because:
- Emails from govdelivery.com domains often pass spam filters due to their legitimate government association
- These emails can successfully pass email authentication protocols like SPF, DKIM, and DMARC
- The government association creates an inherent trust that makes recipients more likely to engage
There is evidence from multiple sources suggesting either security vulnerabilities in the platform or actual breaches of government accounts are being exploited.
3. What should I do if I already clicked a link or connected my wallet?
If you’ve already interacted with one of these phishing attempts:
- If you provided seed phrases or private keys, immediately create a new wallet with a different seed phrase
- Transfer any remaining funds from the compromised wallet to the new wallet immediately
- Disconnect the compromised wallet from all cryptocurrency exchanges and platforms
- Update passwords for any accounts associated with the compromised email
- Report the incident to relevant authorities like the FBI’s Internet Crime Complaint Center (IC3)
- Monitor all accounts for suspicious activity
4. How did scammers get my email address?
The scammers likely obtained email addresses from previous data breaches at cryptocurrency services. Several victims reported receiving these scam emails at addresses they only used for specific cryptocurrency platforms, suggesting targeted data acquisition from various breaches. Some users specifically mentioned receiving these emails at addresses they had only used for exchanges like Bittrex, BlockFi, or even hardware wallet providers like Trezor.
5. Are legitimate bankruptcy proceedings happening for cryptocurrency exchanges?
Yes, both Bittrex and BlockFi have undergone actual bankruptcy proceedings, and legitimate distributions to creditors have occurred. However:
- These legitimate communications come from specific, verified email domains
- They include personalized information about your specific account and claim
- They never request wallet connections or seed phrases
- Distribution amounts differ based on individual claims, not identical across all recipients
If you have legitimate claims in these proceedings, contact the administrators directly through their official websites rather than responding to emails.
Conclusion: Evolution of Cryptocurrency Phishing
The [email protected] scam represents a concerning evolution in cryptocurrency phishing techniques. By exploiting legitimate government communication infrastructure, coordinating across multiple cryptocurrency platforms, and timing attacks to coincide with actual bankruptcy proceedings, these scammers have created a sophisticated operation designed to harvest cryptocurrency credentials.
What makes these campaigns particularly dangerous is their multi-layered approach to establishing legitimacy:
- Using trusted government email domains that bypass security protocols
- Targeting victims of actual cryptocurrency bankruptcies during legitimate payout periods
- Creating professional interfaces that closely mimic official platforms
- Leveraging community confusion about complex bankruptcy proceedings
As cryptocurrency adoption continues to grow, users must maintain heightened awareness regarding communications about their digital assets. The golden rule remains unchanged: legitimate financial administrators will never request your private keys or seed phrases under any circumstances.
By understanding the tactics employed in the [email protected] scam and sharing information through community forums, cryptocurrency users can collectively strengthen their defenses against these increasingly sophisticated phishing attempts. When in doubt, always verify through official channels and remember that unexpected windfalls appearing in your inbox are almost always too good to be true.