Thousands receive fraudulent toll collection notices appearing to come from official Indiana government email addresses
Indiana residents have been inundated with alarming emails claiming to be from [email protected] and other state government addresses warning of unpaid toll fees and threatening account suspensions. State officials have confirmed these messages are fraudulent and part of a sophisticated phishing campaign. Here’s what you need to know to protect yourself.
The Widespread Email Scam Targeting Hoosiers
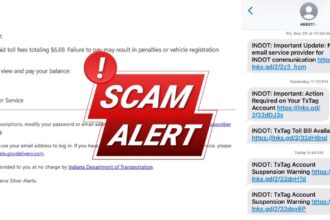
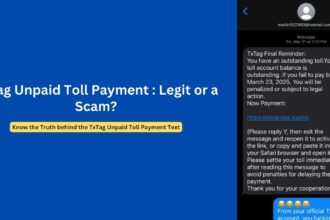
Beginning late Monday night and continuing through Tuesday, May 13, 2025, thousands of Indiana residents and organizations received emails with subject lines like “TxTag Account Suspension Warning” appearing to come from legitimate Indiana government email addresses including [email protected], [email protected], and many others.
The messages claim recipients have unpaid toll fees (commonly $6.69) and warn that “failure to pay may result in penalties or vehicle registration holds.” They contain “Pay Now” buttons or links directing users to fraudulent websites designed to steal personal and financial information.
What makes this scam particularly convincing is that the emails are being sent through infrastructure that legitimately handles government communications. According to technical analysis, these messages are passing through Amazon Web Services (AWS) servers that are authorized to send emails on behalf of subscriptions.in.gov domains.
One Indiana University official reported that over 4,600 of these phishing emails were delivered to iu.edu addresses in a single two-hour window overnight, indicating the massive scale of this campaign.
How the Compromise Happened: Technical Breakdown
The Indiana Office of Technology has confirmed that the fraudulent emails stem from a security breach at a third-party vendor. According to their official statement, the state’s contract with GovDelivery (a platform used by government agencies to manage email communications) ended on December 31, 2024, but the company “did not remove the state’s account from their system.”
A Reddit user with bulk email expertise explained the technical aspects: “At a domain level, the State has public records that say ‘AWS has permission to send email on behalf of subscriptions.in.gov.’ Here the problem with switching to another vendor is that there’s a good chance that the new vendor also sub-contracts AWS to send email. If that’s the case, then it’s correct that the State continues to maintain those records, even if it unfortunately makes it easier for an old vendor account to be used for abuse.”
Granicus, the company that owns GovDelivery, confirmed in a statement that “a contractor’s account was compromised, either through guessing the credentials or the individual was socially engineered into providing them.” They emphasized that “Granicus systems themselves were not breached,” but acknowledged the compromise of an administrative user account.
This security lapse created a perfect opportunity for scammers to send messages that not only appear to come from legitimate government addresses but actually do pass through authorized email channels—making them particularly difficult to detect as fraudulent even by sophisticated email security systems.
Red Flags: How to Identify the Scam Emails
Despite appearing to come from legitimate government sources, these fraudulent messages contain several identifiable red flags:
1. Suspicious “From” Addresses
While the emails appear to come from Indiana government domains like [email protected] or [email protected], legitimate government communications typically come from different address formats.
2. Texas Toll References in Indiana Communications
Perhaps the most obvious red flag is the reference to “TxTag”—a Texas toll collection system—in emails purportedly from Indiana state agencies. Indiana does not use TxTag for toll collection, making this an immediate indication of fraud.
3. Generic or Missing Greetings
Many of the scam emails begin with generic salutations like “Dear Customer” or even blank greetings like “Dear ” (with nothing after it). Legitimate government communications typically address recipients by name.
4. Suspicious Links
The emails contain shortened URLs (often using lnks.gd) or disguised links that redirect to non-government websites. Hovering over these links without clicking would reveal suspicious destinations.
5. Urgent Payment Demands
The messages create false urgency with threats of penalties or vehicle registration holds to pressure recipients into immediate action without careful consideration.
6. Outdated Government References
Some of the emails from the Governor’s Office still reference former Governor Eric Holcomb instead of current Governor Mike Braun, who took office in January 2025, revealing their fraudulent nature.
Official Government Responses and Actions
Multiple Indiana government agencies have responded swiftly to alert residents and mitigate damage:
The Indiana Office of Technology issued a clear warning on their website: “IOT is aware of a Spam Email message circulating that contains ‘TxTag Account Suspension Warning’ in the subject. Please delete these messages as you receive them.” They confirmed that “The State does not send unpaid toll notifications via text or email messages.”
Indiana Attorney General Todd Rokita issued a public alert, stating: “Scammers are relentless in exploiting hardworking Hoosiers, and these fake TxTag emails are no exception. We’re fighting back against fraudsters, but Hoosiers must stay vigilant. Never click links or share personal information from unsolicited emails.”
The Indiana Department of Transportation (INDOT) released an official warning banner instructing recipients to “DO NOT CLICK THE LINK” and “DELETE THE MESSAGE,” while encouraging reporting to the Federal Trade Commission and Internet Crime Complaint Center.
The Indiana Supreme Court also sent notification acknowledging “a malicious email and/or text message being circulated from Indiana state agency GovDelivery accounts,” explicitly warning recipients not to click any links.
State officials are working with Granicus to stop further communications and investigating the full extent of the breach.
Protecting Yourself: What to Do If You Received These Emails
If you’ve received emails claiming to be from [email protected] or other Indiana government addresses regarding TxTag toll payments, here are the steps experts recommend:
If You Haven’t Clicked Any Links:
- Delete the emails immediately
- Do not click any links or reply to the messages
- Flag the email as phishing/spam in your email client to help protect others
- Report the scam to the appropriate authorities (see below)
If You’ve Already Clicked Links or Provided Information:
- Contact your bank or credit card company immediately if you entered payment information
- Change passwords for any accounts that might be compromised
- Monitor your accounts for suspicious activity
- Consider placing a fraud alert on your credit reports
- Run a security scan on any devices used to access the links
Reporting Options:
- Report to the Indiana Attorney General’s Office at www.indianaconsumer.com
- Forward spam emails to the Federal Trade Commission at [email protected]
- File a complaint with the Internet Crime Complaint Center at IC3.gov
- Contact the Indiana Attorney General’s Office at 1-800-382-5516
Frequently Asked Questions
1. Is any email from [email protected] about TxTag or toll payments legitimate?
No. The Indiana Office of Technology has explicitly confirmed that “The State does not send unpaid toll notifications via text or email messages.” Any email claiming to be from [email protected] or other state domains regarding toll payments is fraudulent.
2. Why are these scam emails so convincing?
These emails are particularly convincing because they are actually being sent through legitimate email infrastructure. Due to a security breach at a former state contractor (GovDelivery), scammers gained access to an account authorized to send emails that appear to come from official Indiana government addresses. This means the emails may pass standard security checks and even appear “clean” to some email security systems.
3. How did scammers get access to send emails that appear to be from [email protected]?
According to official statements, the State of Indiana’s contract with GovDelivery (owned by Granicus) ended on December 31, 2024, but the company failed to remove the state’s account from their system. A contractor’s account was then compromised, giving scammers access to send emails via Amazon Web Services servers that are authorized to deliver emails on behalf of [email protected] and other state domains.
4. Could my personal information be at risk even if I didn’t click any links?
If you only received the email but didn’t click links or provide information, your personal data related to this specific incident is likely secure. However, the fact that scammers obtained your email address may indicate it was exposed in a data breach. It’s always a good practice to regularly monitor your accounts for suspicious activity.
5. What should I do if I’ve already provided payment information by clicking a link in these emails?
If you’ve entered credit card or payment information on a website linked from these emails, contact your bank or credit card company immediately to halt payments and replace your card. Monitor your accounts closely for unauthorized charges, consider placing a fraud alert on your credit reports, and file reports with both the Indiana Attorney General’s Office and the FTC.
Conclusion: A Reminder to Stay Vigilant
The TxTag account suspension warning emails appearing to come from [email protected] represent a sophisticated phishing campaign that exploits trusted government communication channels. This incident highlights the evolving nature of cyber threats and the importance of maintaining vigilance even when messages appear to come from official sources.
What makes this scam particularly concerning is how it exploits technical infrastructure legitimately used for government communications. The compromise of a former vendor’s account enabled scammers to send messages through authorized channels, creating a convincing façade of legitimacy.
As digital communications continue to evolve, so too do the tactics of cybercriminals. This incident serves as a powerful reminder that verification through official channels is essential before responding to any message requesting payment or personal information—regardless of how legitimate it may appear.
The good news is that state officials have responded quickly to alert residents and are working to prevent further fraudulent messages. By staying informed and following the protective measures outlined above, Indiana residents can safeguard themselves against this and future scam attempts.
Remember: When in doubt, don’t click, don’t share information, and verify directly through official websites or phone numbers you know to be legitimate.