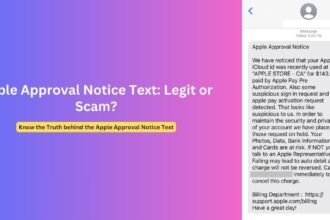
A sophisticated phishing scam impersonating PayPal representative “Richard Ostrom” is spreading through DocuSign’s email delivery system, security researchers warn. This scam joins a growing wave of attacks exploiting DocuSign’s trusted status to bypass email security filters and target unsuspecting users. The scheme combines social engineering tactics with legitimate-looking DocuSign infrastructure to steal financial information and potentially gain remote access to victims’ devices.
The Rise of DocuSign-Based PayPal Phishing
Since January 2025, cybersecurity experts have observed a significant surge in phishing attacks leveraging DocuSign’s platform to distribute fraudulent PayPal notifications. These attacks are particularly dangerous because they successfully authenticate through standard email security protocols like SPF, DKIM, and DMARC, making them appear legitimate to both automated systems and human recipients.
The “Richard Ostrom” campaign represents the latest evolution of this threat, using a specific sender identity to create an impression of legitimacy. According to multiple IT administrators posting on security forums, these emails appear to originate from legitimate DocuSign servers with the domain “docusign.net” but contain suspicious content designed to alarm recipients about fictitious PayPal transactions.
“What makes these attacks particularly effective is their abuse of trusted platforms,” explains cybersecurity analyst Maya Henderson. “When users see the DocuSign brand, they inherently let their guard down because it’s a service they recognize and trust for legitimate business.”
Overview of the Richard Ostrom DocuSign Scam
The scam operates through a multi-stage process designed to create urgency and bypass typical security awareness:
- Initial Contact: Victims receive an email appearing to come from “Richard Ostrom via DocuSign” with a subject line mentioning suspicious PayPal account activity, often referencing cryptocurrency transactions.
- False Urgency: The email claims to detect unauthorized Bitcoin purchases (typically around $599) or other suspicious transactions on the recipient’s PayPal account.
- Legitimate Infrastructure Abuse: The email contains actual DocuSign links that direct to authentic DocuSign pages hosting malicious content.
- Phone-Based Attack: Rather than immediately requesting credentials, these scams often direct victims to call a “PayPal Resolution Center” phone number supposedly for account verification.
- Information Harvesting: During the call, scammers request sensitive information including account credentials, personal details, and sometimes attempt to establish remote access connections to the victim’s device.
One IT administrator who examined the email headers confirmed, “These messages are genuinely passing through DocuSign’s mail servers, which is why they’re successfully authenticating against standard email security measures. The email headers show legitimate DocuSign origination points.”
Latest Patterns in Fake “Richard Ostrom” Emails
The fraudulent emails follow several consistent patterns that can help users identify them as scams:
- Sender Information: Emails typically come from an address like “[email protected]” but display a sender name of “Richard Ostrom via DocuSign”
- Subject Line Themes: Common subject lines include:
- “Your PayPal Account Shows Suspicious Bitcoin Activity”
- “Urgent: Unverified Transaction on Your PayPal Account”
- “PayPal Security Alert: Action Required”
- Document Structure: The email presents as a DocuSign document requiring review, with a prominent “REVIEW DOCUMENT” button
- Transaction Details: Specific transaction amounts (commonly $599.00) with crypto-related purchases, creating an impression of legitimacy through detail
- Toll-Free Numbers: Includes a “PayPal Resolution Center” phone number that is typically toll-free and available “24/7”
Data from email security providers suggests this campaign has sent millions of messages since early 2025. According to one security forum post, a single organization blocked 291 suspicious DocuSign.net emails in a 30-day period, many featuring similar characteristics to the “Richard Ostrom” campaign.
Red Flags That Expose the Scam
Despite the sophisticated nature of these attacks, several warning signs can help users identify fraudulent communications:
1. Mismatched Brand Practices
PayPal does not typically use DocuSign to communicate about account security issues. Any notification about account security would be delivered directly through PayPal’s own notification system or the PayPal app.
2. Cryptocurrency Emphasis
The prominent mention of cryptocurrency transactions is a deliberate tactic. Crypto-related scams create immediate concern due to the irreversible nature of blockchain transactions, prompting users to act quickly without careful consideration.
3. Phone-Based Resolution
Legitimate financial institutions rarely instruct customers to call immediately about specific transactions. Instead, they would direct users to log into their accounts through official applications or websites to review flagged activity.
4. Unusual Recipient Addresses
Many recipients have noticed the emails are sent to strange or generic addresses like “Dear Customer [email protected]” rather than their actual email addresses, indicating bulk phishing rather than targeted communication.
5. Pressure Tactics
The emails contain urgent language emphasizing immediate action and threatening account restrictions if rapid steps aren’t taken, a classic social engineering technique to override critical thinking.
Protecting Yourself from DocuSign-PayPal Scams
Security experts recommend several measures to protect against these sophisticated phishing attempts:
1. Verify Through Official Channels
Never use contact information provided in suspicious emails. Instead, open a new browser window and manually navigate to the official PayPal website or app to check your account status and transaction history.
“The most effective defense is ignoring the communication path offered by the scammer,” says cybersecurity expert James Chen. “Always establish your own secure connection to verify any concerning account notifications.”
2. Implement Enhanced Email Filtering
Organizations should consider creating custom filtering rules for DocuSign messages containing suspicious keywords like “PayPal,” “Bitcoin,” “transaction,” or “unauthorized.” Multiple IT professionals report success with this approach.
3. Enable Multi-Factor Authentication
Activate MFA on both PayPal and DocuSign accounts to add an additional security layer, making it significantly harder for scammers to gain unauthorized access even if they obtain passwords.
4. Report Suspicious Activities
Forward suspicious emails to:
- [email protected] (for DocuSign-related phishing)
- [email protected] (for PayPal impersonation attempts)
“Reporting these emails helps both companies improve their detection systems,” notes digital security advocate Elena Rodriguez. “It’s a small step that contributes to collective security.”
5. Educate About Voice Phishing (Vishing)
Since these scams often involve phone calls, users should understand that legitimate financial institutions never ask for complete passwords, PINs, or authentication codes over the phone. Hang up immediately if such requests are made.
What To Do If You’ve Been Targeted
If you’ve interacted with a suspicious “Richard Ostrom” email or similar DocuSign-PayPal communications, take these immediate steps:
- Change Passwords: Immediately change passwords for PayPal and any other financial accounts, using unique, strong passwords for each service.
- Contact PayPal Directly: Report the incident through PayPal’s official fraud reporting channels (through the app or website, not the phone number in the suspicious email).
- Monitor Account Activity: Closely watch for unauthorized transactions on all financial accounts for several weeks following exposure.
- Freeze Credit: Consider placing a temporary fraud alert or credit freeze with major credit bureaus if you shared sensitive personal information.
- Full Security Scan: Run comprehensive malware scans on any devices used to access the suspicious email or communicate with potential scammers.
- Enable Transaction Alerts: Set up notifications for all account activities to quickly identify any unauthorized transactions.
Several victims report that scammers are increasingly requesting remote access to devices under the guise of “verifying account information” or “securing the account,” which can lead to installation of persistent malware or complete account takeovers.
Frequently Asked Questions
1. Is any email from Richard Ostrom at PayPal legitimate?
No. PayPal does not currently employ a representative named “Richard Ostrom” who sends DocuSign emails about account security. This name appears to be fabricated specifically for this phishing campaign.
2. Why are scammers using DocuSign instead of direct emails?
DocuSign has high deliverability rates and trust status with most email systems. By leveraging DocuSign’s infrastructure, scammers can bypass many email security filters and appear more legitimate to recipients.
3. Can I trust emails that pass SPF, DKIM, and DMARC authentication?
While these authentication methods verify that an email came from the claimed domain (in this case, docusign.net), they don’t validate the actual content of the message. Scammers are exploiting legitimate DocuSign accounts to send malicious content.
4. What information are these scammers typically trying to steal?
The primary targets are PayPal login credentials, banking information, personal identification details, and sometimes remote access to devices. Some variants attempt to trick victims into making direct payments to “reverse unauthorized transactions.”
5. Has DocuSign acknowledged this issue?
Yes. DocuSign has acknowledged the abuse of their platform and recommends reporting suspicious emails to [email protected]. They also maintain an incident reporting guide at docusign.com/trust/security/incident-reporting.
The Broader Threat Landscape
The “Richard Ostrom” campaign represents a troubling trend in phishing attacks that security researchers call “trusted platform abuse.” By infiltrating or abusing legitimate services with established reputations, attackers create scenarios where both automated security systems and human intuition are more likely to fail.
“We’re seeing a significant shift toward these hybrid attacks,” explains cybersecurity researcher Dr. Marcus Williams. “Rather than creating obviously fake domains or completely fabricated emails, attackers are finding ways to leverage the infrastructure and trust of established platforms.”
This evolution presents unique challenges for traditional security approaches. Email security systems typically whitelist domains with good reputations, like docusign.net, making it difficult to block malicious content without also blocking legitimate business communications.
Some security providers report that telephone-based threats have seen particular growth, with one security service detecting more than 1.6 million telephone-based scams in a recent 30-day period. These voice phishing or “vishing” attacks often begin with email communications but move quickly to phone conversations where social engineering techniques can be more effective.
Conclusion: Vigilance in a Changing Threat Environment
The sophisticated nature of the “Richard Ostrom” PayPal-DocuSign phishing campaign highlights the evolving tactics of modern cybercriminals. As attackers increasingly leverage trusted platforms and multi-channel approaches, traditional security advice like “check the sender’s email address” becomes insufficient.
Effective protection now requires a layered approach combining technical controls, organizational policies, and—most importantly—ongoing education about emerging threats. Organizations should regularly update security awareness training to include information about trusted platform abuse and multi-channel attacks that combine email, documents, and telephone interactions.
As one security forum participant noted, “The days of obvious Nigerian prince scams are long gone. Today’s phishing attempts are professionally crafted, technically sophisticated, and psychologically manipulative.”
By understanding the specific mechanics of scams like the “Richard Ostrom” campaign, users and organizations can develop more effective detection and prevention strategies to protect sensitive information and financial assets.
For the latest updates on emerging phishing threats, visit our cybersecurity resource center at shoppersvila.com.
Disclaimer: This article is provided for informational purposes only and does not constitute legal or professional security advice. Names and specific details of phishing campaigns may change as attackers adapt their techniques.