In an era of increasing cyber threats, many Microsoft users find themselves bombarded with unexpected single-use code emails. These messages, appearing to come from Microsoft’s legitimate domains, have sparked confusion and concern among users worldwide. While some are genuine security measures, others may be part of sophisticated phishing attempts. This comprehensive guide explores the phenomenon of Microsoft single-use code emails, distinguishing between legitimate security features and potential scams.
The Mystery of Unsolicited Microsoft Single Use Code Email Scam
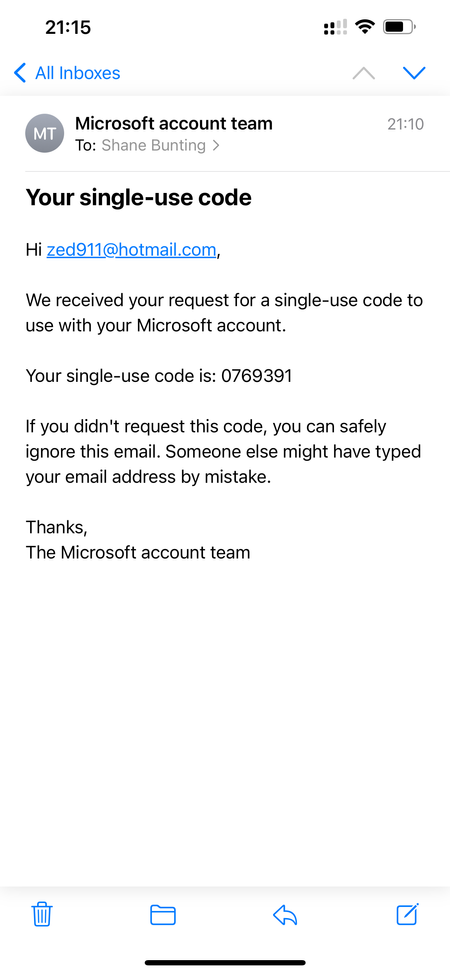
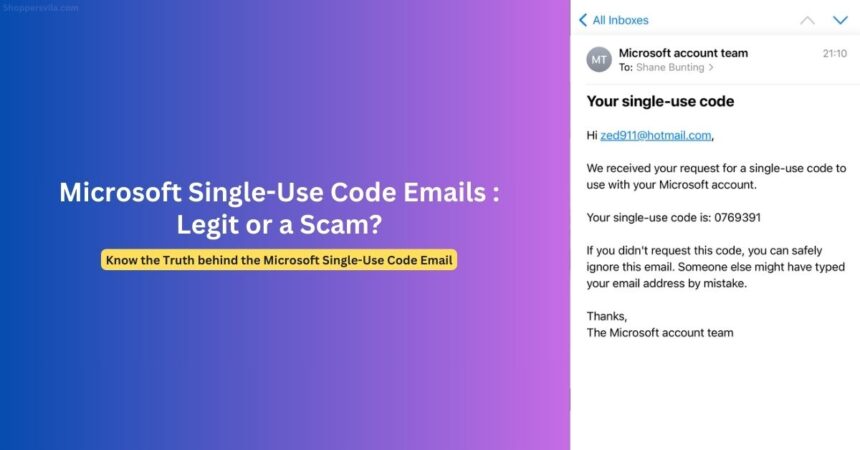
For thousands of users globally, opening their inbox to find multiple Microsoft single-use code emails has become a daily occurrence. These messages typically read: “We received your request for a single-use code to use with your Microsoft account,” followed by a numeric code and instructions to ignore the email if the recipient didn’t request it.
The frequency can be alarming – some users report receiving upwards of 10 such emails daily for weeks or even months. The pressing question becomes: Are these legitimate Microsoft communications, or is something more sinister at play?
The truth is nuanced. Most of these emails are actually legitimate Microsoft communications triggered by various activities related to your Microsoft identity ecosystem, but understanding their source is crucial to protecting your digital security.
Understanding Legitimate Microsoft Single-Use Codes
Microsoft’s single-use code system is a fundamental security feature designed to protect user accounts. These codes are triggered in several legitimate scenarios:
- New Sign-In Attempts: When logging into a Microsoft account from a new device, location, or browser
- Password Reset Requests: During the account recovery process
- Security Information Updates: When making changes to account security settings
- Unusual Activity Detection: Microsoft’s security systems detecting potentially suspicious behavior
- Recovery Email Verification: When your email is listed as a recovery option for other Microsoft accounts
The last point represents a key insight discovered by users who investigated persistent code emails. Many people unknowingly have their current email address listed as a recovery option for old, forgotten Microsoft accounts. When these dormant accounts are targeted in credential stuffing attacks, it generates single-use codes to the recovery email address.
How Cybercriminals Exploit Microsoft’s Security Features
While the single-use code system is designed for protection, cybercriminals have developed ways to leverage it for malicious purposes:
1. Credential Stuffing Attacks
Using databases of leaked email/password combinations, automated systems attempt to access thousands of Microsoft accounts simultaneously. When these attempts trigger security measures, legitimate code emails are sent to the account holders or recovery emails.
2. Phishing Through Familiarity
Seeing frequent legitimate security emails can desensitize users, making them more vulnerable to carefully crafted phishing attempts that mimic the format of genuine Microsoft emails but contain malicious links.
3. Social Engineering
Some scammers directly contact users by phone or other means, claiming to be from Microsoft support and requesting the code that was just sent to “verify identity” – a tactic that circumvents the protection the code was meant to provide.
4. Data Breach Exploitation
Cybercriminals specifically target accounts whose credentials appeared in known data breaches, assuming (often correctly) that users reuse passwords across multiple services.
Red Flags: Distinguishing Legitimate Emails from Scams
While most single-use code emails are legitimate Microsoft communications, detecting fraudulent ones requires attention to detail:
| Legitimate Microsoft Emails | Potential Scam Indicators |
|---|---|
| Sender address ends with microsoft.com | Slight variations like microsoft-team.com or m1crosoft.com |
| Simple, text-based format | Overly elaborate formatting with multiple images |
| Includes only a code, no clickable links | Contains urgent calls to action with embedded links |
| Explicitly states to ignore if you didn’t request it | Creates urgency about account compromise |
| Never asks for personal information | Requests additional personal details or credentials |
| Does not threaten account closure | Contains threats about account suspension |
Additional warning signs of fraudulent emails include:
- Grammatical errors or unusual phrasing
- Generic greetings rather than your name or email
- Requests to download attachments
- Pressure to act quickly to avoid consequences
- Different code formats than Microsoft’s standard 7-digit numeric codes
What To Do If You Receive Microsoft Single-Use Code Emails
If you find yourself receiving multiple Microsoft single-use code emails, follow these steps:
1. Verify the Source
Check the sender’s email address carefully. Legitimate Microsoft security notifications come from addresses ending with microsoft.com. Examine the email headers if you’re technically inclined.
2. Do Not Share the Code
Under no circumstances should you share the code with anyone, including people claiming to be from Microsoft support. Legitimate Microsoft employees will never ask for your security codes.
3. Check Your Account Activity
Log into your Microsoft account directly (not through any links in emails) and check your recent activity:
- Visit account.live.com/Activity
- Review for any unrecognized access attempts
- Check devices that have recently connected to your account
4. Find Connected Accounts
If you’re receiving persistent code emails without suspicious activity on your main account, investigate forgotten accounts where your email might be listed as a recovery option:
- Use the “forgot Microsoft account username” form with your current email
- Microsoft will display accounts associated with your email
- Log into these accounts and update recovery information or close them
5. Secure Your Main Account
Take proactive security measures:
- Change your password to a strong, unique combination
- Enable two-factor authentication
- Remove your email as a recovery option from accounts you no longer use
- Consider using a password manager
Protecting Yourself From Future Attacks
Building robust digital security practices can help prevent account compromise:
1. Use Unique Passwords For Each Service
Password reuse across multiple services is the single biggest vulnerability exploited in these attacks. Use a password manager to create and store unique credentials for each service.
2. Enable Advanced Security Features
Microsoft offers several enhanced security options:
- Microsoft Authenticator app for passwordless sign-in
- Security key authentication
- Advanced threat protection with Microsoft 365 subscriptions
3. Regularly Check Data Breach Status
Visit haveibeenpwned.com to check if your email addresses have appeared in known data breaches, and change passwords for any affected services.
4. Create Email Filters
While addressing the root cause, create email filters to automatically categorize or archive legitimate Microsoft security emails to reduce inbox clutter.
5. Keep Software Updated
Ensure your operating system, browsers, and security software have the latest updates to protect against known vulnerabilities.
What To Do If You’ve Been Compromised
If you suspect your Microsoft account has been accessed without authorization:
- Immediately Change Your Password Access account.microsoft.com and change your password, ensuring it’s unique and complex.
- Review Account Activity Check for unauthorized changes to recovery information, security settings, or unusual sign-ins.
- Scan Your Devices Run a comprehensive malware scan on all devices used to access your Microsoft account.
- Check Connected Applications Review and remove any suspicious applications with access to your Microsoft account.
- Contact Microsoft Support For serious breaches, contact Microsoft support directly for additional assistance.
- Monitor Financial Accounts If your Microsoft account is connected to payment methods, monitor those accounts for unauthorized charges.
The Bigger Picture: Data Breach Ecosystem
The flood of Microsoft single-use code emails represents a symptom of the broader data breach ecosystem. When credentials are leaked from one service, attackers systematically attempt to use them across popular platforms like Microsoft, assuming password reuse.
This underscores the importance of cybersecurity hygiene across all services, not just Microsoft. A vulnerability in one account can cascade to others if proper security measures aren’t implemented consistently.
Conclusion
The majority of unexpected Microsoft single-use code emails are legitimate security measures responding to actual login attempts – often to forgotten accounts linked to your email. While annoying, they actually demonstrate that Microsoft’s security systems are functioning as designed, preventing unauthorized access.
By understanding the source of these emails and taking appropriate action, users can not only reduce the flood of notifications but also strengthen their overall digital security posture. The key is distinguishing between legitimate security communications and potential scams, then addressing the root causes rather than merely treating the symptoms.
Remember that in the digital age, vigilance and proactive security measures are your best defense against increasingly sophisticated cyber threats.