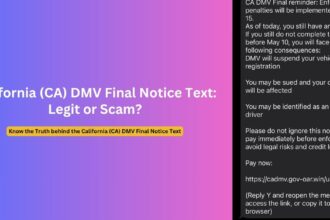
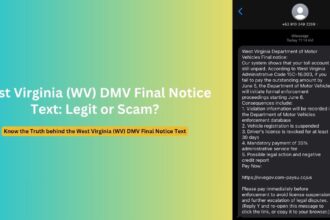
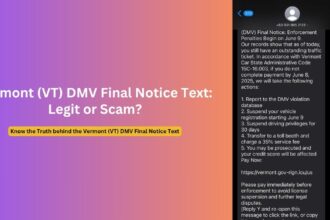
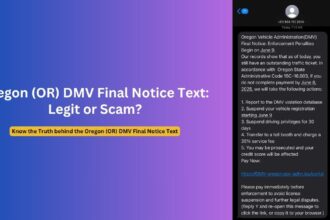
In an alarming trend of cybercrime, sophisticated scammers are weaponizing the reputation of the Internet Crime Complaint Center (IC3), a trusted cybercrime reporting platform operated by the FBI. These malicious actors have developed intricate schemes designed to exploit victims’ trust, stealing personal information and financial resources through elaborate impersonation tactics.
Overview of Internet Crime Complaint Center (IC3) Impersonation Scam
The IC3 impersonation scam is a multi-layered digital fraud strategy where cybercriminals create highly convincing fake communications purporting to be from the legitimate Internet Crime Complaint Center. These scams typically involve:
- Fabricated restitution claims
- Fake legal proceedings
- Promises of substantial monetary compensation
- Sophisticated social engineering techniques
How Scammers Trap Innocent Victims
Scammers employ several psychological manipulation techniques to ensnare unsuspecting individuals:
- Authority Impersonation
- Use official-looking letterheads
- Mimic government communication styles
- Include fake case numbers and references
- Leverage perceived legitimacy of law enforcement agencies
- Emotional Manipulation
- Create scenarios of past financial victimization
- Offer seemingly compassionate “compensation”
- Generate a sense of urgency
- Trigger fear or excitement to cloud judgment
Red Flags: Identifying IC3 Impersonation Scams
Warning Signs in Communication
| Red Flag | Explanation |
|---|---|
| Unsolicited Communication | Legitimate agencies rarely initiate contact about unknown cases |
| Request for Personal Information | Official bodies won’t ask for sensitive details via email |
| Grammatical Errors | Professional communications maintain high linguistic standards |
| Pressure to Act Quickly | Scammers create artificial time constraints |
| Suspicious Email Addresses | Non-official domains or multiple contact points |
Protecting Yourself: Comprehensive Defense Strategies
Immediate Actions for Suspected Scam Encounters
If you receive a suspicious IC3-related communication:
- Do Not Respond Directly
- Avoid clicking links
- Do not download attachments
- Refrain from providing personal information
- Verify Independently
- Contact IC3 through official channels (www.ic3.gov)
- Use official FBI contact information
- Report the suspicious communication
- Document Everything
- Save email headers
- Screenshot communications
- Preserve all evidence for potential investigation
Data Breach and Extended Scam Tactics
Cybercriminals utilize multiple sophisticated methods beyond IC3 impersonation:
- Social Media Exploitation
- Creating fake law enforcement pages
- Harvesting personal information
- Spreading misinformation
- Multi-Platform Approach
- Coordinated email, phone, and text message campaigns
- Cross-referencing stolen personal data
- Creating intricate backstories for fraudulent claims
Comprehensive Protection: Your Digital Safety Toolkit
Proactive Cybersecurity Measures
- Personal Information Management
- Limit public personal data exposure
- Use privacy settings on social platforms
- Be cautious about sharing personal details online
- Technical Safeguards
- Install reputable antivirus software
- Keep systems and applications updated
- Use strong, unique passwords
- Enable two-factor authentication
- Continuous Education
- Stay informed about emerging scam techniques
- Attend cybersecurity webinars
- Follow trusted cybersecurity resources
What to Do If Scammed: Immediate Recovery Steps
Incident Response Checklist
- Financial Protection
- Contact your bank immediately
- Freeze potentially compromised accounts
- Report fraudulent transactions
- Request new credit/debit cards
- Legal and Official Reporting
- File a complaint with IC3 (www.ic3.gov)
- Report to local law enforcement
- Contact Federal Trade Commission (FTC)
- Consider identity theft protection services
- Digital Forensics
- Change all online passwords
- Scan devices for malware
- Monitor credit reports
- Consider professional cybersecurity consultation
Final Thoughts: Vigilance is Your Best Defense
The IC3 impersonation scam represents a sophisticated digital threat requiring constant awareness and proactive defense. By understanding these tactics, maintaining skepticism, and following comprehensive protection strategies, individuals can significantly reduce their vulnerability to such malicious schemes.
Remember: No legitimate government agency will demand immediate action, request sensitive information via unsecured channels, or promise unrealistic financial compensation.
Stay informed, stay skeptical, stay safe.